
Читайте также:
|
Overview
Check Point’s firewall contains several capabilities – filtering traffic based on source / destination, searching for viruses, making sure that sensitive information doesn’t leak, etc.
These capabilities are implemented by ‘software blades’ – each software blade implements one of these capabilities.
Each blade receives a Message, an object which includes the following members:
1. From, to [int] – source and destination of the message.
2. Protocol [int] (Valid range is [0, 255]) – identifies the protocol of this message.
There are 256 protocols numbered 0 to 255.
3. Data [String, variable length] – Data, protocol specific.
The message is supplied to the blade via the handleMessage function. This function should decide whether the message is supposed to be allowed / dropped, and return this decision as the function return value (‘ACCEPT_MESSAGE’ for allow, ’DROP_MESSAGE’ for drop). Your mission is to implement these blades.
During this test, you’ll implement the following blades –
· Firewall blade – the firewall blade blocks any message coming from a well known blacklisted sender / recipient.
· Anti Virus blade – looks for virus signatures in the messages data, and blocks messages with viruses.
· Data Loss Prevention (DLP) blade – looks for confidential information which is sent from the organization to an outside address, and blocks it.
· Monitoring blade -The monitor blade doesn’t filter (it accepts all traffic), but rather maintains updated statistics about the protocols seen.
General instructions, tips and tricks
· The different blades are independent – error in one blade implementation unlikely to affect the others (unless it is a crash / memory overrun, of course).
· You are provided with a tester, which runs the various blades and displays the results. You need to implement only the blades specified below. While you can see and debug the tester code, it is unlikely to help you in implementing the blades.
· You can run the tester with only part of the blades, by providing the following command argument:
o 1000 - firewall blade, 0100 – Anti Virus, 0010 – DLP, 0001 – Monitoring
o Combinations are supported (e.g. 1001 – Firewall and monitoring)
o See at the "Basic HOWTO" section at the end of this document for instructions on how to configure the command arguments.
· Working with the IDE:
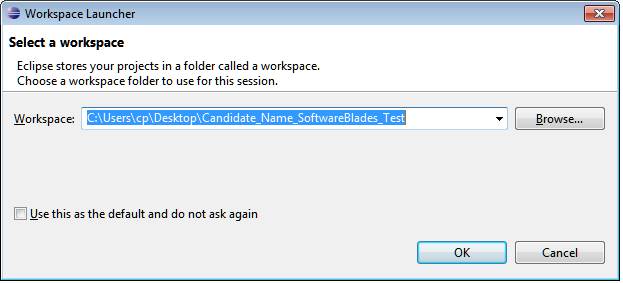
In such a case click the “Browse…” button and select the directory where your test resides (The directory name starts with your name and ends with _SoftwareBlades_Test. In the example below the name of the candidate is John Doe.)
Example:

o The code located under the com.checkpoint.blades_test.ReadOnly_DoNotChange package is for reference only, and in most cases can be ignored.
Дата добавления: 2015-09-11; просмотров: 79 | Поможем написать вашу работу | Нарушение авторских прав |